The voice characteristics of every individual depend on the anatomy of their throat. Voice biometrics utilizes these speaker-specific voice features to authenticate users. If you are wondering how passive voice biometrics works, read on.
Passive Voice Biometrics: The Workings
In passive voice biometrics, the user is authenticated seamlessly in the background without their knowledge. The process of passive authentication starts with capturing the user’s voice and extracting speaker-specific voiceprints. To obtain reference voiceprints, the minimum required user speech is less than ten seconds. Subsequent authentications use the reference voiceprint to verify the authenticity of the claimed user. This is flexible to be carried out in both the IVR phase and the agent phase of the call.
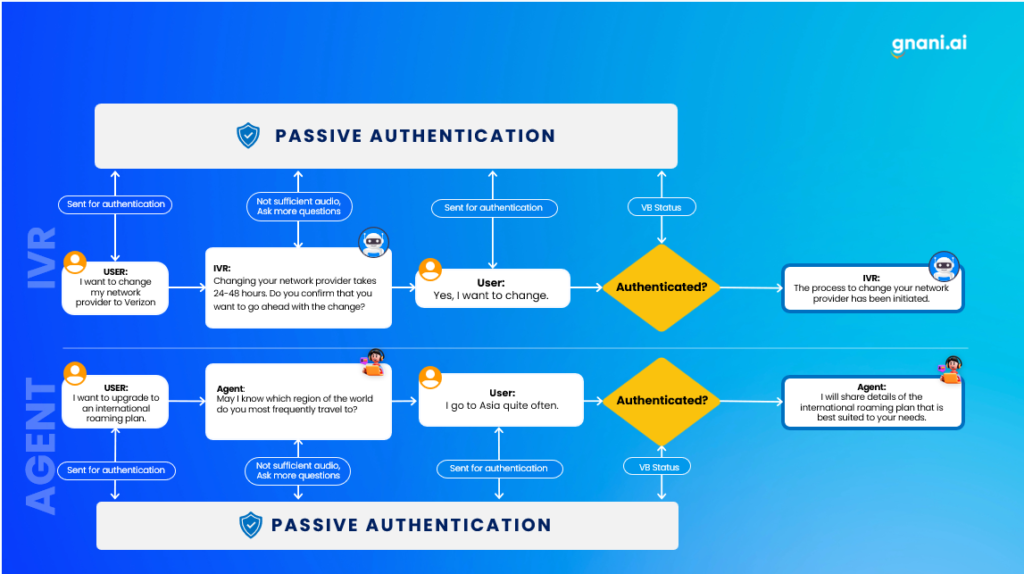
The unique feature of passive voice authentication is that no PINs or passwords are required to authenticate users. This is why it is harder to breach than other authentication methods.
Passive Voice Biometrics: One of The Safest Authentication Methods
Why is passive voice biometrics one of the safest authentication methods?
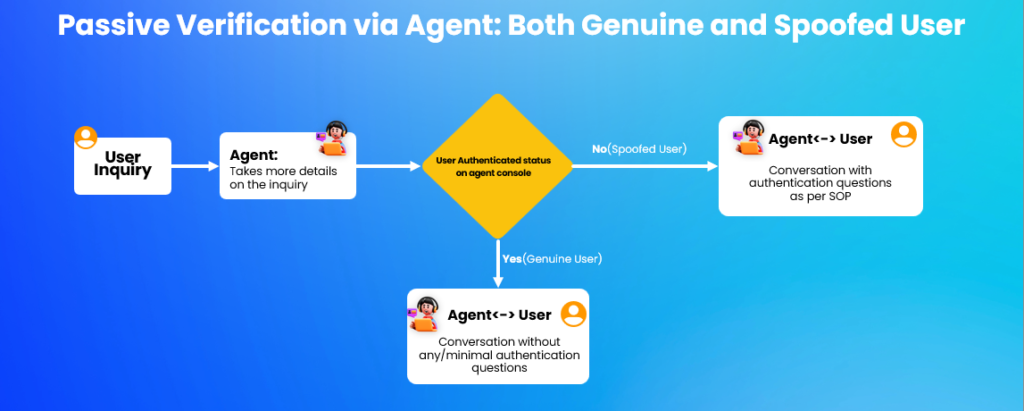
Passive voice authentication tools like Gnani.ai’s Armour365 is advanced enough to detect and stop bruteforce attacks, replay attacks, synthetic attacks, mimicry, liveness and bots. Gnani.ai’s Armour365 is language agnostic so it authenticates users using their speaker-specific voice features instead of traditional authentication methods like passwords or codes.
Advantages of Passive Voice Authentication
- Users can be authenticated using free speech so the hassle of remembering passwords and PINs can be avoided completely.
- Passive voice authentication has made it very convenient to authenticate remote users securely.
- Since it is language agnostic, it can be used for a diverse demographic without any customizations.
- Users can be authenticated in just a second. So, this makes the whole process smoother and efficient.
- Users are protected against bruteforce, replay, and synthetic attacks.
Click here to check out Gnani.ai’s voice authentication tool.


